
#
Getting Started in Cybersecurity
How to break into Cybersecurity? 🔒 Here's what I tell people who ask me this question.
People often want to "hack stuff" immediately, but there are essential foundations you need first. Here's a realistic roadmap:
#
The Prerequisites
You'll need solid fundamentals in three areas:
- Linux systems (Ubuntu, Kali, etc.)
- Networking (DNS, IP, routing, firewalls)
- Programming (Python, Bash, or PowerShell)
Operating System 💡
Don't stay confined to one OS, get comfortable with Windows (Desktop & Server), Linux, and macOS if possible.
#
Where to Learn (Free & Paid)
TryHackMe
https://tryhackme.com
Start here. Most labs run directly in your browser, and you can choose learning paths based on your interests. Free content available, premium plan ~$20/month. Their Learning Roadmap shows different cyber careers so you can find your fit.
HackTheBox
https://www.hackthebox.com
Once you have basics down, move here for more challenging vulnerable servers. Watch write-ups first to understand the methodology, then redo the machine. This builds real hacking intuition.
PortSwigger Academy (for web pentesting)
https://portswigger.net/web-security
Free, guided lessons on web vulnerabilities. BurpSuite Community is free too.
RootMe (French-friendly)
https://www.root-me.org
Challenge-based platform with accessible difficulty levels.
#
YouTube Channels Worth Following
- TCM Security Academy – clear, practice-oriented content
- NetworkChuck – fun IT & cyber vulgarization
- John Hammond – hands-on: malware, CTF, challenges
- David Bombal – networking fundamentals & IT concepts
#
The Secret Weapon: Documentation
This is CRITICAL. Use Notion, Obsidian, or Evernote to document:
- Commands you discover
- Your attack methodology
- What worked AND what didn't
- Tools and their use cases
Your notes become your personal knowledge base. This matters more than most people realize.
#
Building Your Network & Visibility
- Share what you're learning on LinkedIn (success AND failures)
- Attend local events: BSides Montréal, NorthSec, HackFest, CyberEco, GoSec, InCyber
- Connect with people from these communities
- Help other beginners, you'll learn twice as fast
- And for those with head too big for their hoodie, remember where you are coming from 😉
Remember 💡
In cybersecurity, nobody knows everything.
#
Set a Realistic Schedule
Spend 30 minutes to 1 hour daily. You can't learn all this in school. Plan for evening study sessions. This is a marathon, not a sprint.
Remember 💡
It's ok to take a break.
#
Your Path Forward
- Master fundamentals (Linux, networking, programming)
- Start with TryHackMe learning paths
- Move to HackTheBox as you progress
- Document everything obsessively
- Get involved in the community
- Consider certifications later (Security+, eJPT, OSCP)
Got questions? Google is your first resource, the answers are usually out there. If you get stuck, feel free to reach out.
#
AI In all of this ?
As AI I mean LLM stuff
Well, It's everywhere and i beleive that we should use all the available ressources out there to help us in this journey. But there is a catch.
- ✔️ Use AI as a tool
- ❌ Don't let AI do everything for you, you wont learn that way
- ✔️ Use AI to build your flascards and learning path
- ✔️ Use AI for question BUT make sure to double check the commands before using them
- ❌ Don't copy/paste AI stuff without checking it
#
The Dunning–Kruger Effect in Cybersecurity
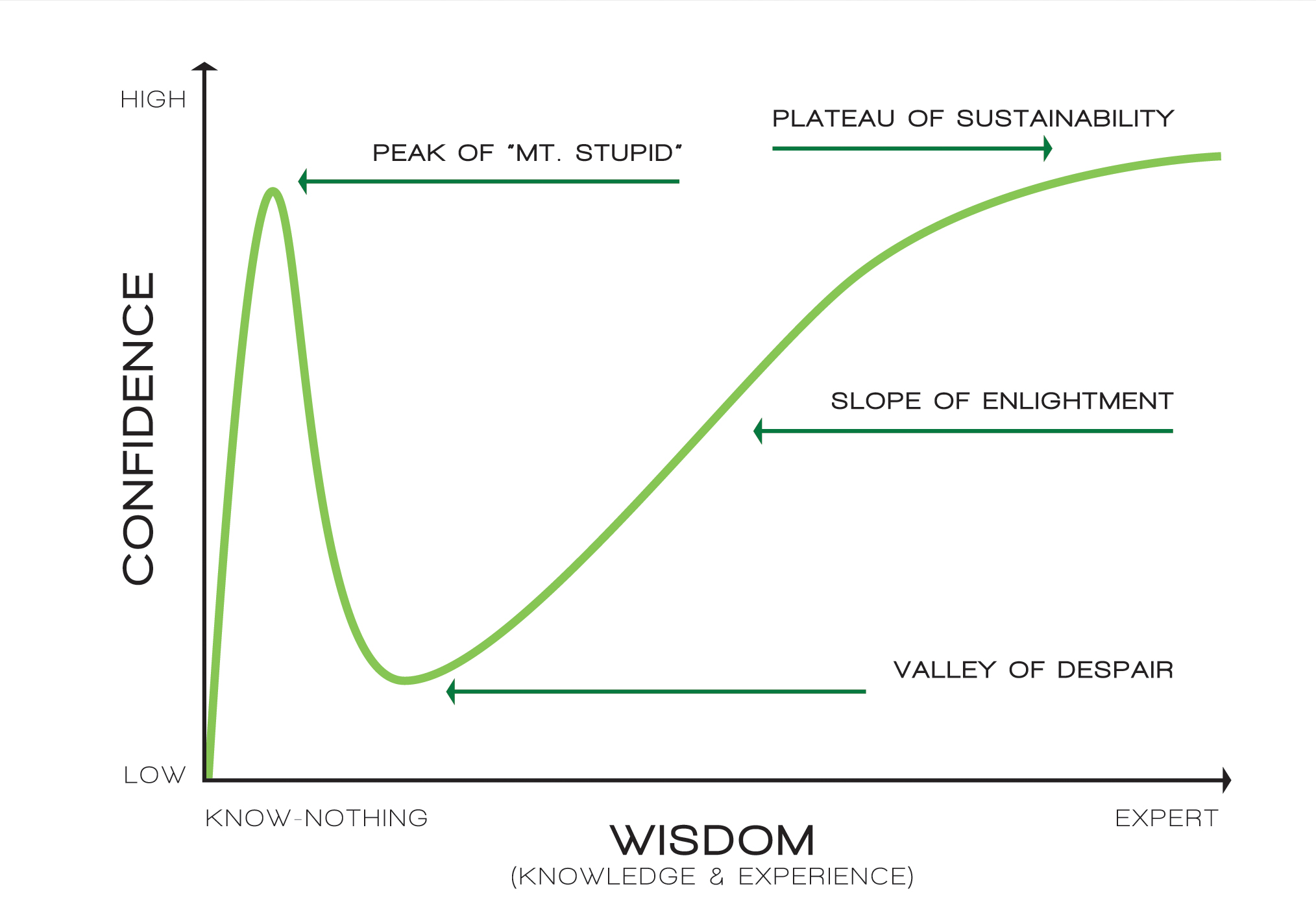
What it is
The Dunning–Kruger effect describes how people with low expertise tend to overestimate their competence, while high performers often underestimate theirs due to better awareness of complexity and unknowns.
How it shows up
- Early learners feel "ready to hack anything" after first wins (e.g., easy CTFs), mistaking narrow success for broad mastery.
- Intermediate practitioners become more cautious as they discover edge cases, real-world constraints, and failure modes.
- Experienced professionals communicate uncertainty, qualify assessments, and emphasize methodology over single "tricks".
Risks in practice
- Overconfidence drives unsafe testing, scope violations, and misinterpretation of scan results as exploitable "vulns".
- Underconfidence can suppress responsible reporting, public sharing, or applying for roles where skills are adequate.
Practical safeguards
- Maintain a learning log with assumptions, evidence, and post-mortems to calibrate self-assessment.
- Seek structured feedback: code reviews, pentest peer reviews, and CTF write-up critiques.
- Use benchmarked paths and labs (difficulty laddering) to avoid confusing novelty with depth.
- Separate tooling proficiency from problem-solving and threat-modeling competency in self-evaluations.
- Regularly teach or write-explaining forces confrontation with gaps and unknowns.
Healthy mindset
- Treat confidence as a hypothesis that must be tested against diverse scenarios, not a feeling earned from isolated wins.
- Prefer falsifiable claims: "Given these constraints and evidence, here’s the most likely path," with explicit limits and next steps.
